re:solution vs Atlassian Data Center SAML SSO
Spot Every Difference
resolution’s SAML SSO offers endless options to customize your configuration, while Atlassian’s preinstalled SSO is a one-size-fits-all.
But don’t take our word for it – the truth is in the details.
Use this guide to explore how you can solve your specific needs and make the best decision for your Data Center environments.
I cannot express enough how much I appreciate how much heavy lifting these scripts do, but our team is only 2 people, and we manage 6 prod instances completely end-to-end (Tier 1-4) for ~5000 users. You enable a tiny team to deliver big things.
Timothy Ryner, National Geospatial-Intelligence Agency
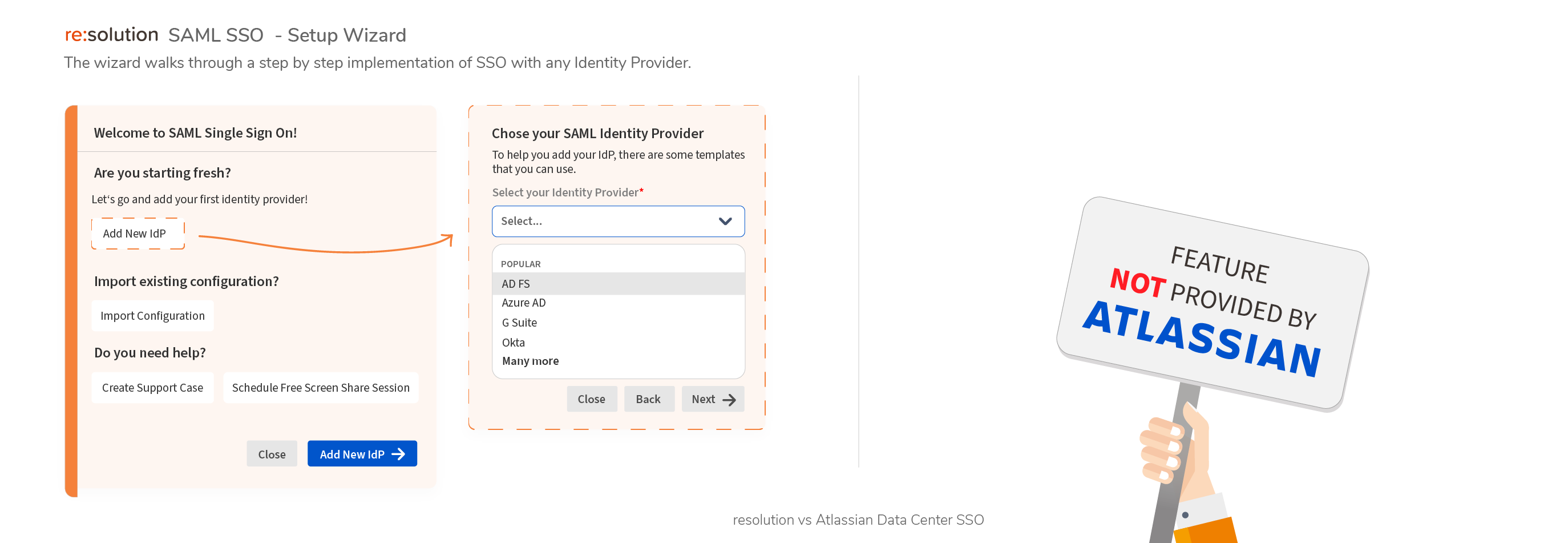
1. Setup
Guided Configuration
- Easily configure your SAML SSO, guided by setup wizard
- Identity Specific guides for major providers
Manual configuration only, without IdP specific guides
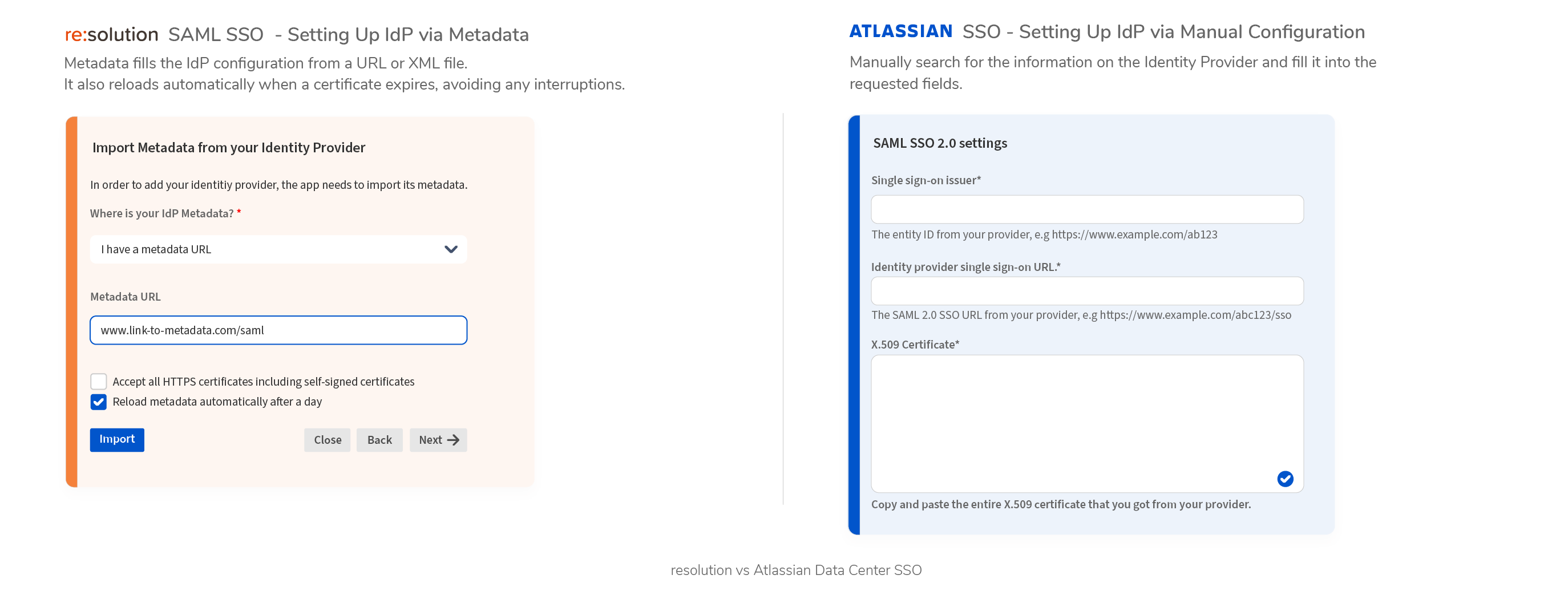
Setting up IdP via Metadata
- Reload Metadata automatically based on a configurable interval to avoid interruptions due to expired certificates
- SAML IdPs with HTTP POST and REDIRECT bindings are supported
- Metadata is not supported
- Certificates must be modified manually after expiration
- Only SAML IdPs with HTTP POST binding are supported
Single Logout
- Ability to logout user from IdP and other Applications when logging out of the Atlassian applications
- Ability to honor logout requests from IdP when the user logged out of other application
- Not supported
- Logout only terminates the Atlassian session
- Logging out from IdP or via IdP does not close the Atlassian applications (potential security risk)
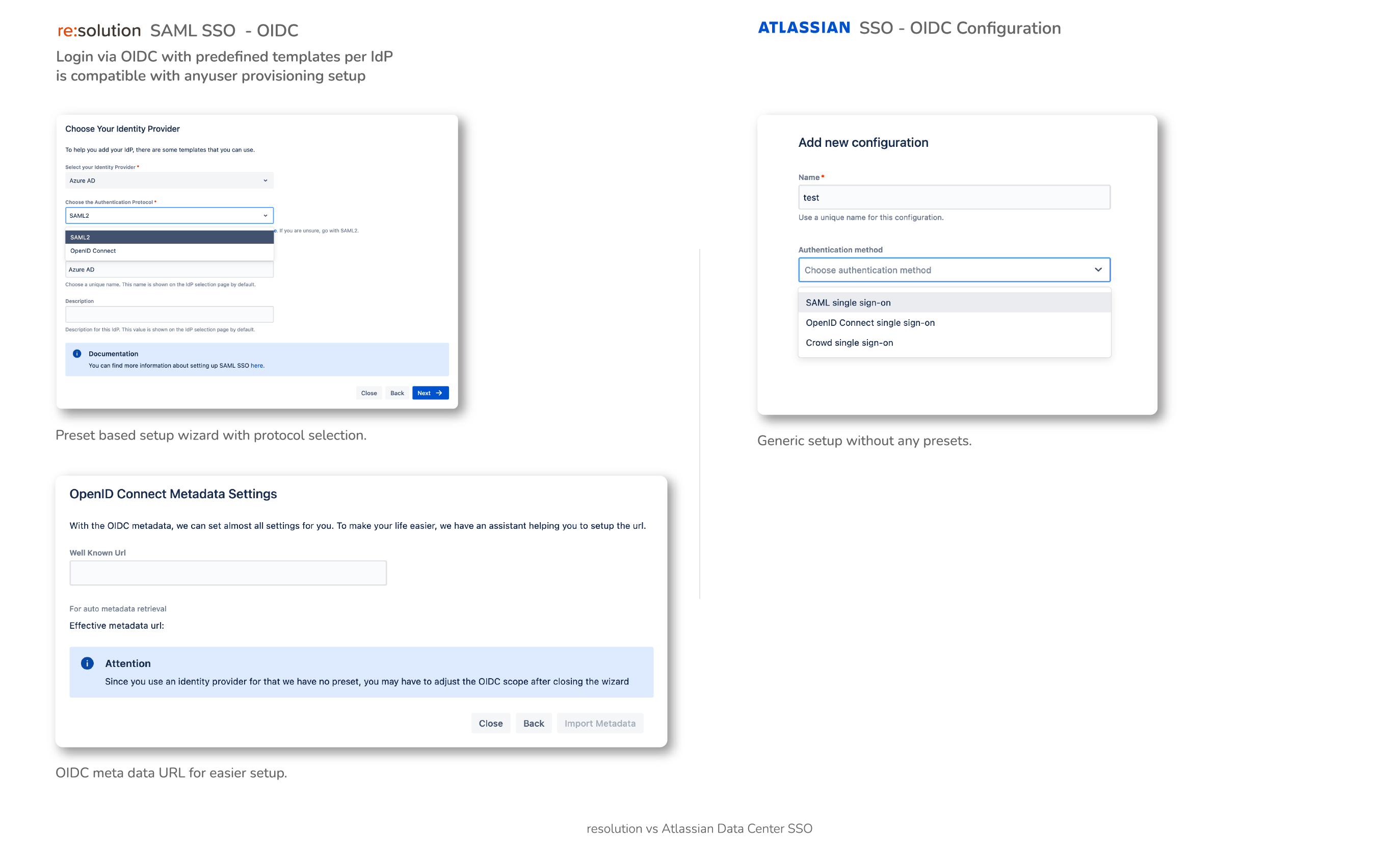
2. Additional Login Protocols
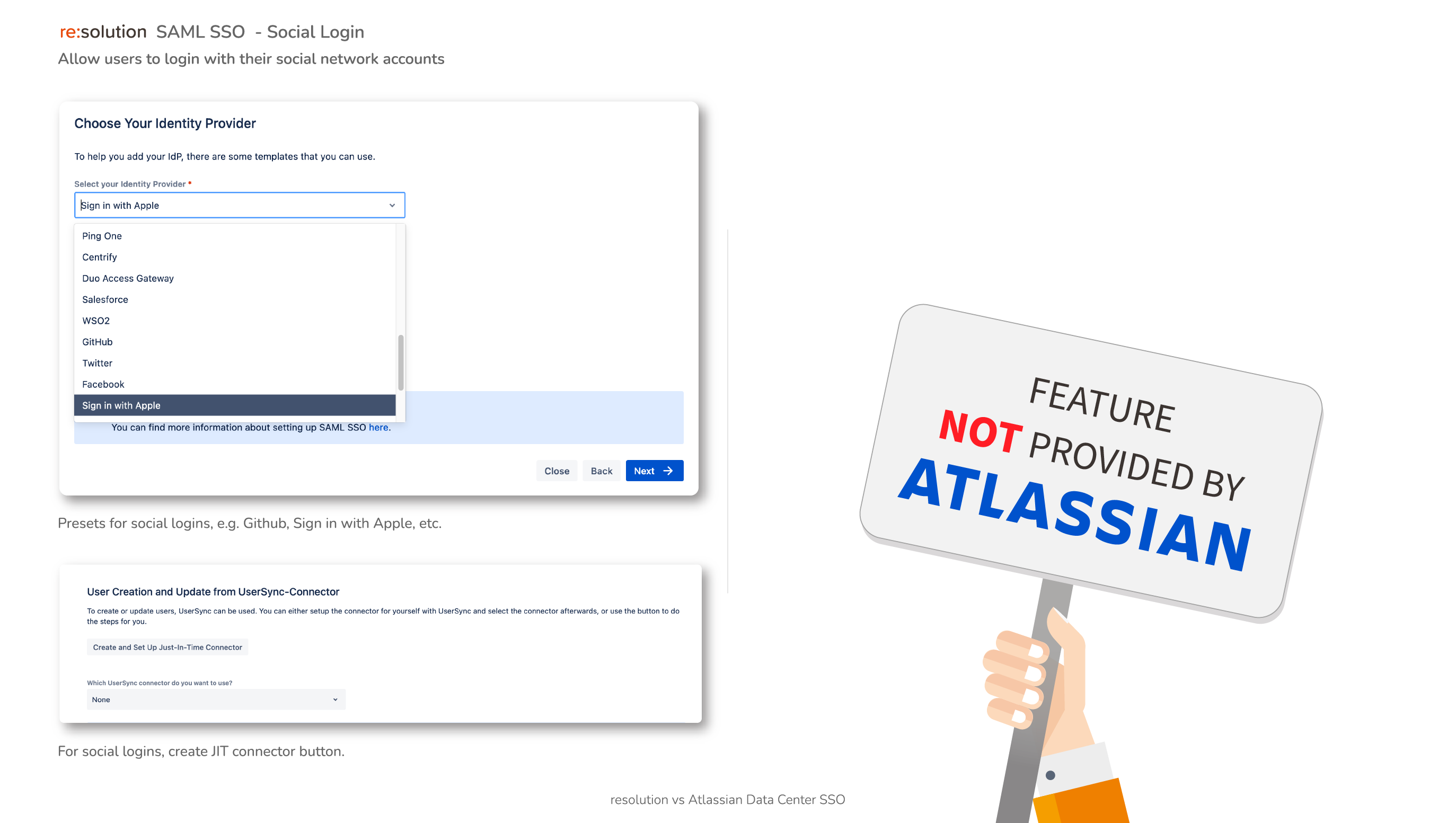
Social Login
With social login, big projects can be open to the public and anybody can join them using their existing social identities
- Social logins with Atlassian Cloud, facebook, Linkedin, github, and Apple
- OAuth2 logins can be connected
- Enable Just in Time provisioning with a custom button
Not provided
3. User Provisioning
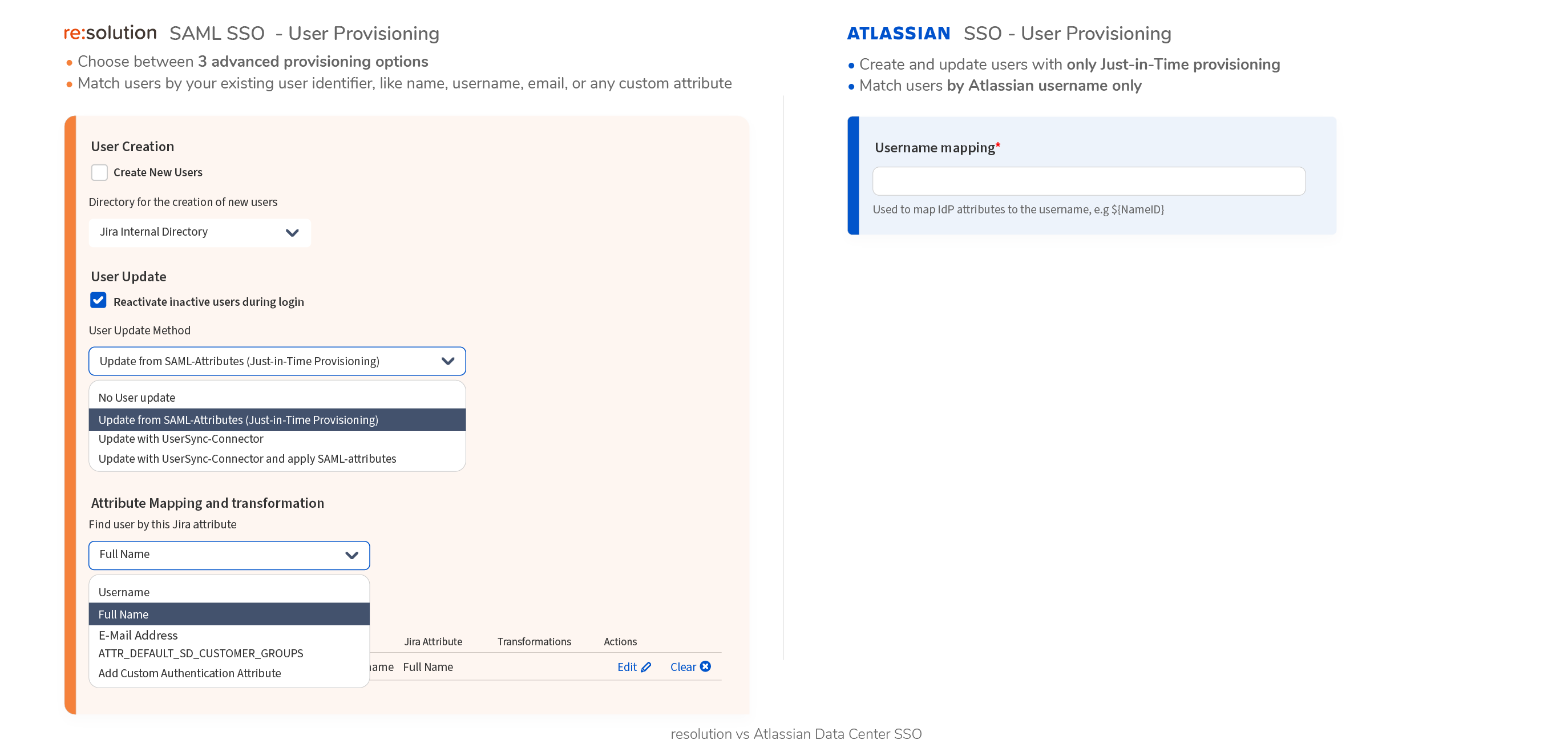
Choose User Creation & Update Method
- Just-in-Time (JiT) Provisioning Creating the User based on values from the SAML-response during login.
- User Sync-Connector Synchronize individual users as they login or synchronize entire directories ahead of time. Supports filtering options.
- Hybrid – Update with the User Sync connector and apply SAML attributes Can combine the best of both worlds – information from User Sync & from the SAML response
Read More
- Update/Create a user with Just-in-Time provisioning
- Search user account by Username only
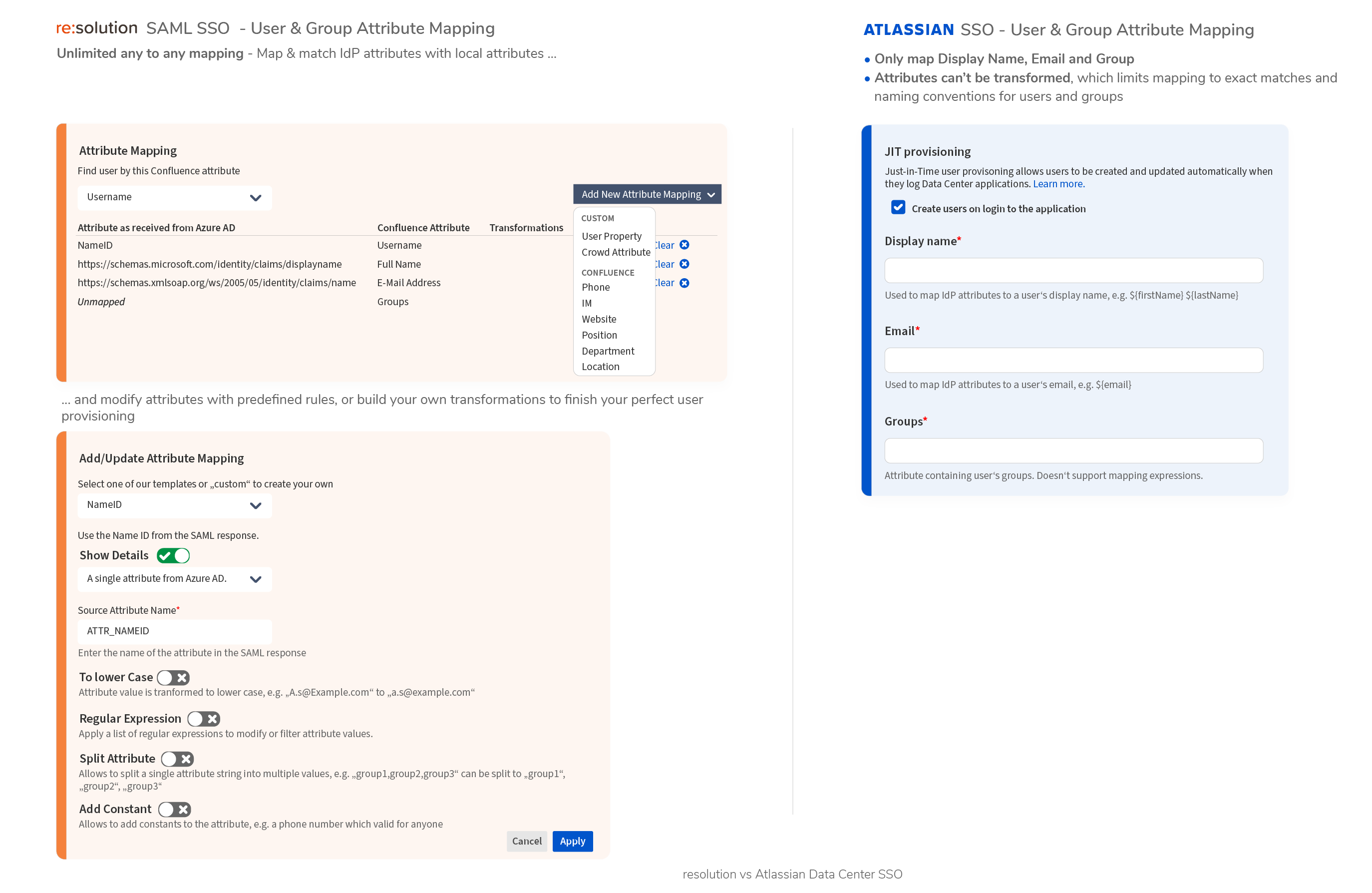
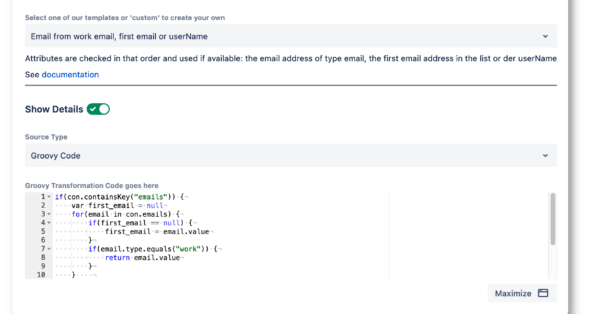
Attribute mapping & transformation for users and groups
- Map and match any IdP attribute to any local attribute into Confluence Profiles, including for example location or phone
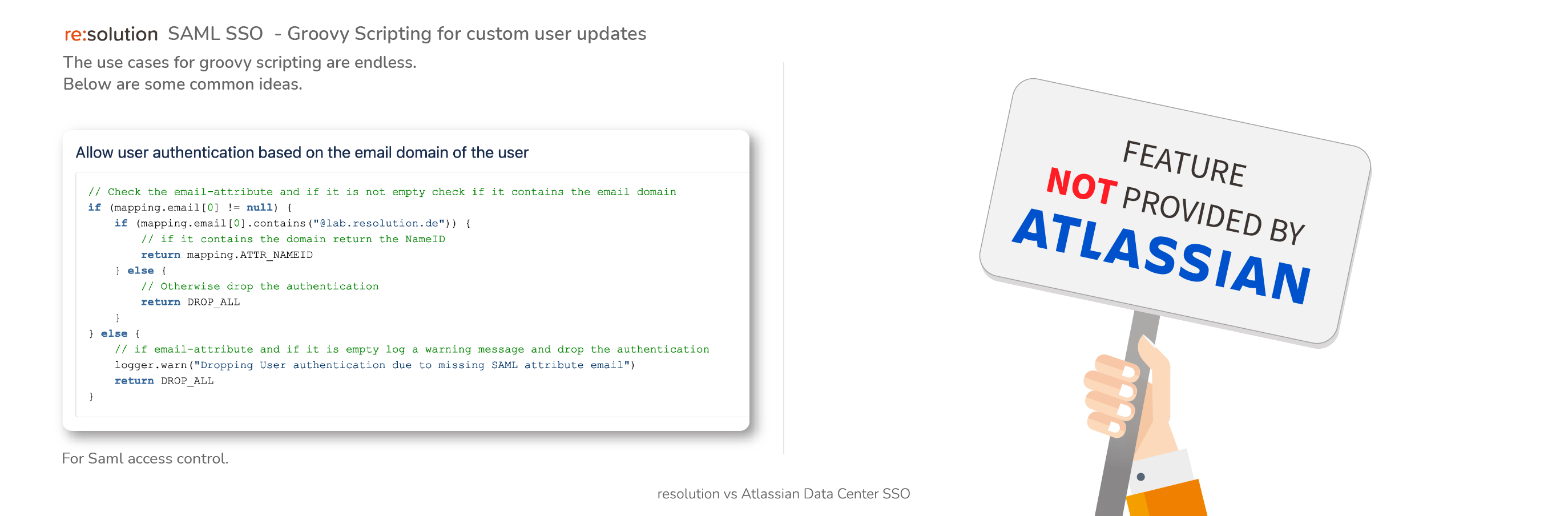
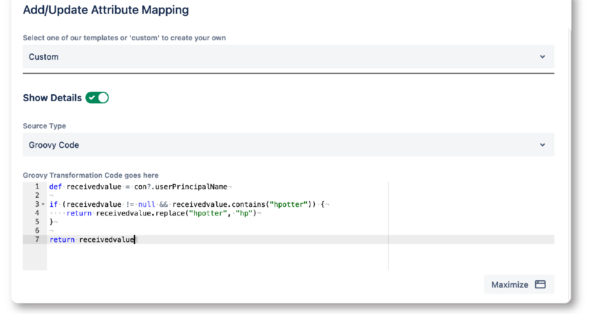
- Attributes can be modified ( “transformed”) according to rules i.e., domain names removed, attributes combined, alternatives chosen – custom logic with Groovy scripts is supported
- Integrations with popular Apps like LinchPin User Profile, Scriptrunner, etc.
- Distinguishes between users created with SAML and local users for JiT update
- Choose the directory where new users should be stored
Only Display Name, EMail obtained from the SAML response during Just in Time(JiT) Provisioning.
- No modifications or transformations are possible
Advanced Group Settings
- Option to switch on/off automatic group creation & group membership removal
- Assign default groups with a dropdown Menu
- Configure Jira Service Desk Groups & Organisation
- Groups are created and removed during login automatically (can’t be configured)
- No user interface available, happens by default without being configurable
4. User Synchronization
User Synchronization
Further Examples (click to enlarge):
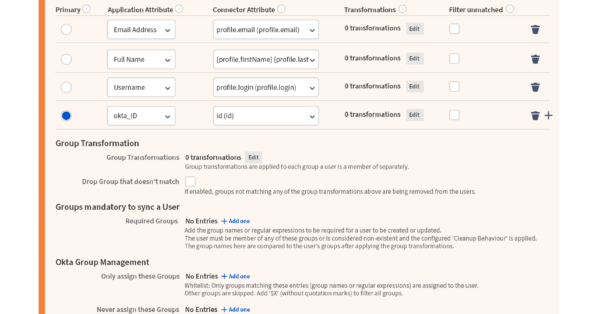
- User Name Transformation & Group Name Transformation
- Add attributes from the Identity Provider’s API and write them to the Atlassian Application’s fields or User Property values. Supports advanced mapping and transformation (see section 2)
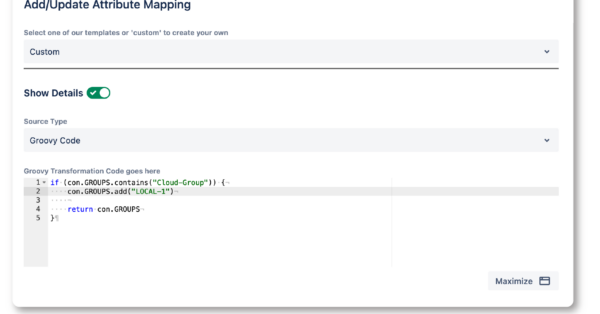
- Configure how groups are sent from the IdP, and how to keep or overwrite local groups
- Easily write custom connectors to external cloud applications in Groovy
- Supports SCIM 2.0
- Synchronize Profile Pictures
Sync large directories up to 20x faster with Server Side and Local Filtering. Applies when only a fraction of the cloud directories needs to be updated i.e., sync 3 of 100,000 groups in a 20,000 user instance.
Not supported
Groovy scripting
Further Examples (click to enlarge):
- Transformations.
Examples:
– Remove special characters from the username
– SCIM: parse multiple attributes to find all email address that should be attached to that user - Add or remove attributes and groups based on conditions.
Example: Assign users to some local groups if they are member of some IdP group - Govern access control.
Example: Deny synchronization if the user seats exceed the current tier limit
Not supported
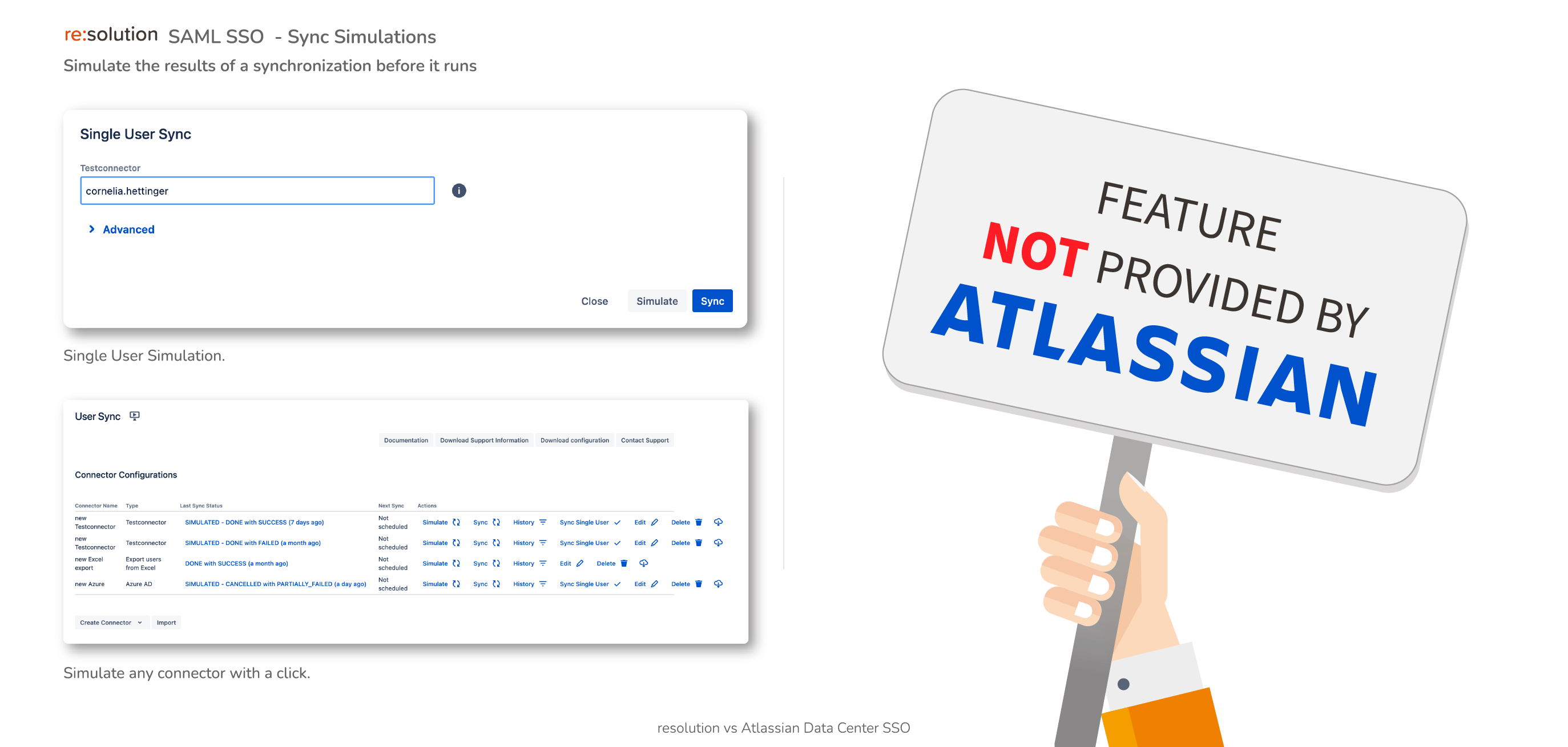
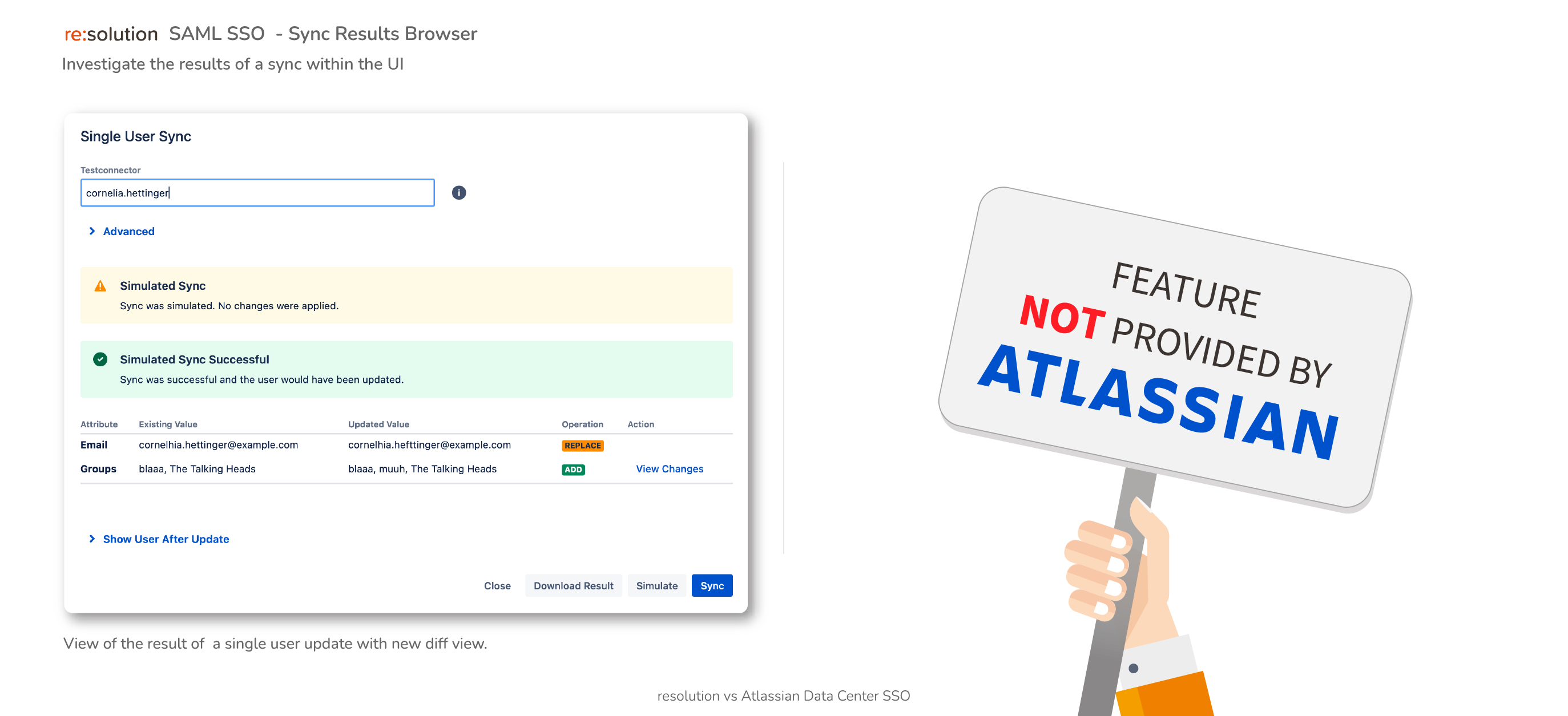
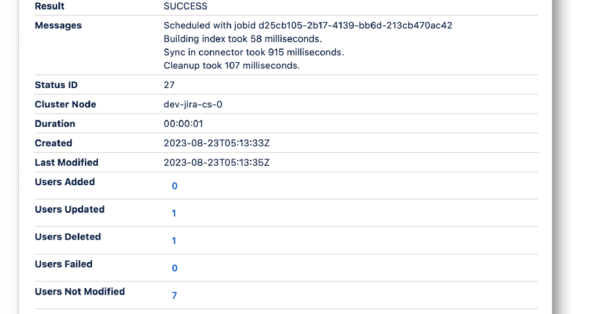
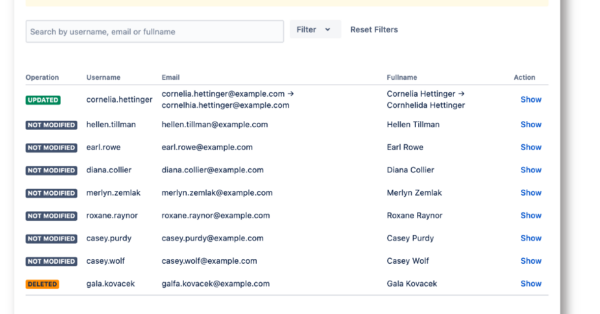
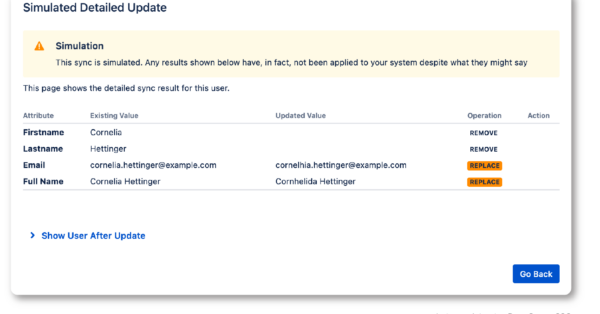
Sync Result Browser (coming soon)
Further Examples (click to enlarge):
- UI Viewer of any synchronization
- Spot sync issues easily
- UI substitute for the traditional JSON file containing every sync detail
Not supported
5. User Deactivation
Automatic User Deactivation
Combining Just-in-Time Provisioning with ‘Disable inactive user connector.’
- Automatically deactivate multiple users
- Automatically remove users from groups
- Exclude members of specific groups from deactivation/ group removal
- Filter users on last activity date and deactivate manually
- Receive reports when users are deactivated
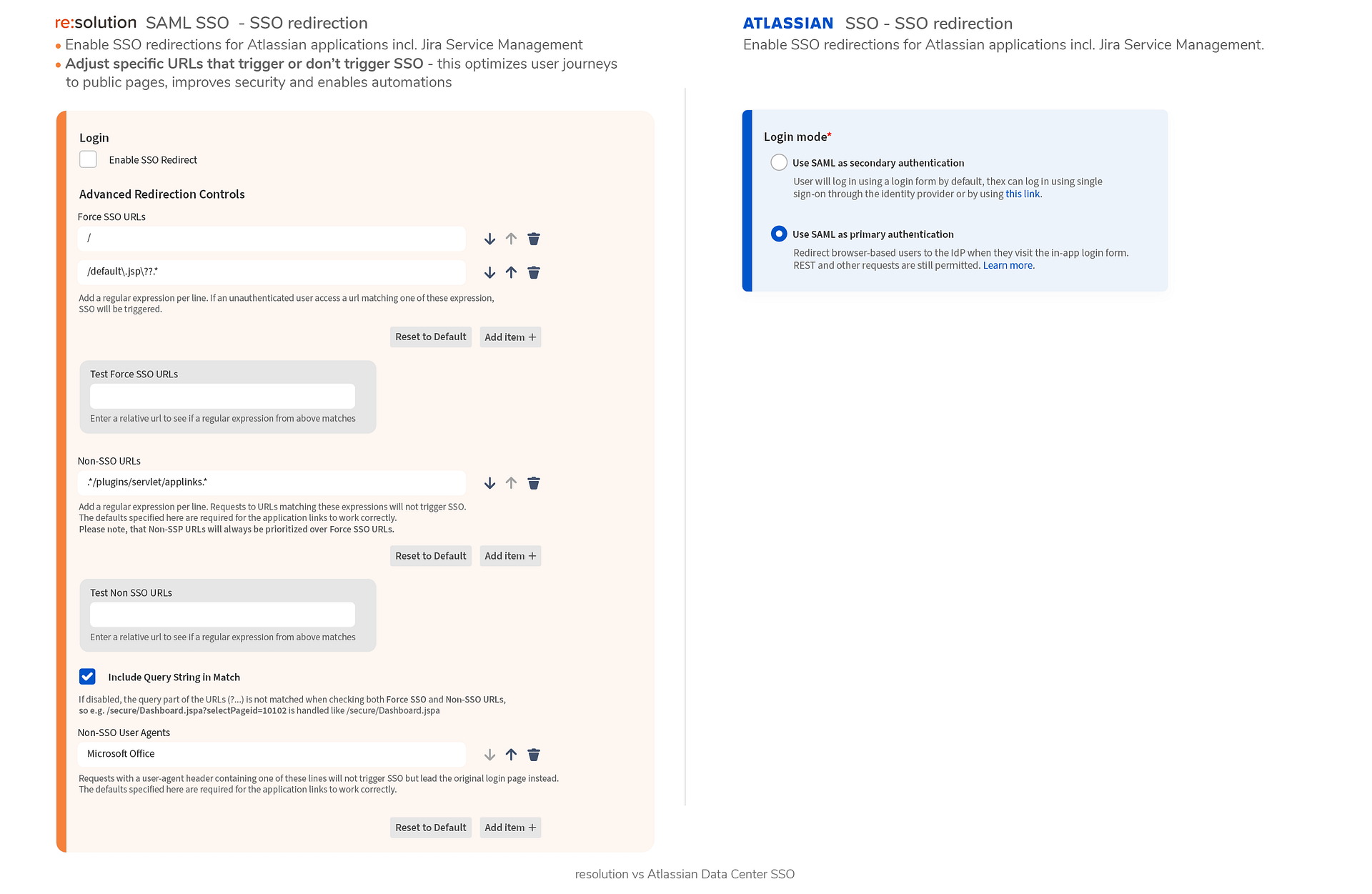
6. SSO Redirection
Regular Login On Demand
- Enable Non-SSO (bypass SAML with a special link), for example for administration access
- Unchecking the option disables password-based authentication
Redirection can be activated through both the user interface and REST requests
Redirection can be only activated with REST requests or database changes
SSO Redirection
- Enable SSO redirections
- Enable SSO redirections for Service Desk Customers
- Define specific URLs that trigger SSO
- Define specific URLs that do not trigger SSO
- Define User-Agent headers that do not trigger SSO
- Customizable buttons for redirection for each IdP configuration. I.e.: “Click here if you are a customer”, “Click here if you are contractor”
- Enable SSO redirections
- Enable SSO redirections for Service Desk Customers
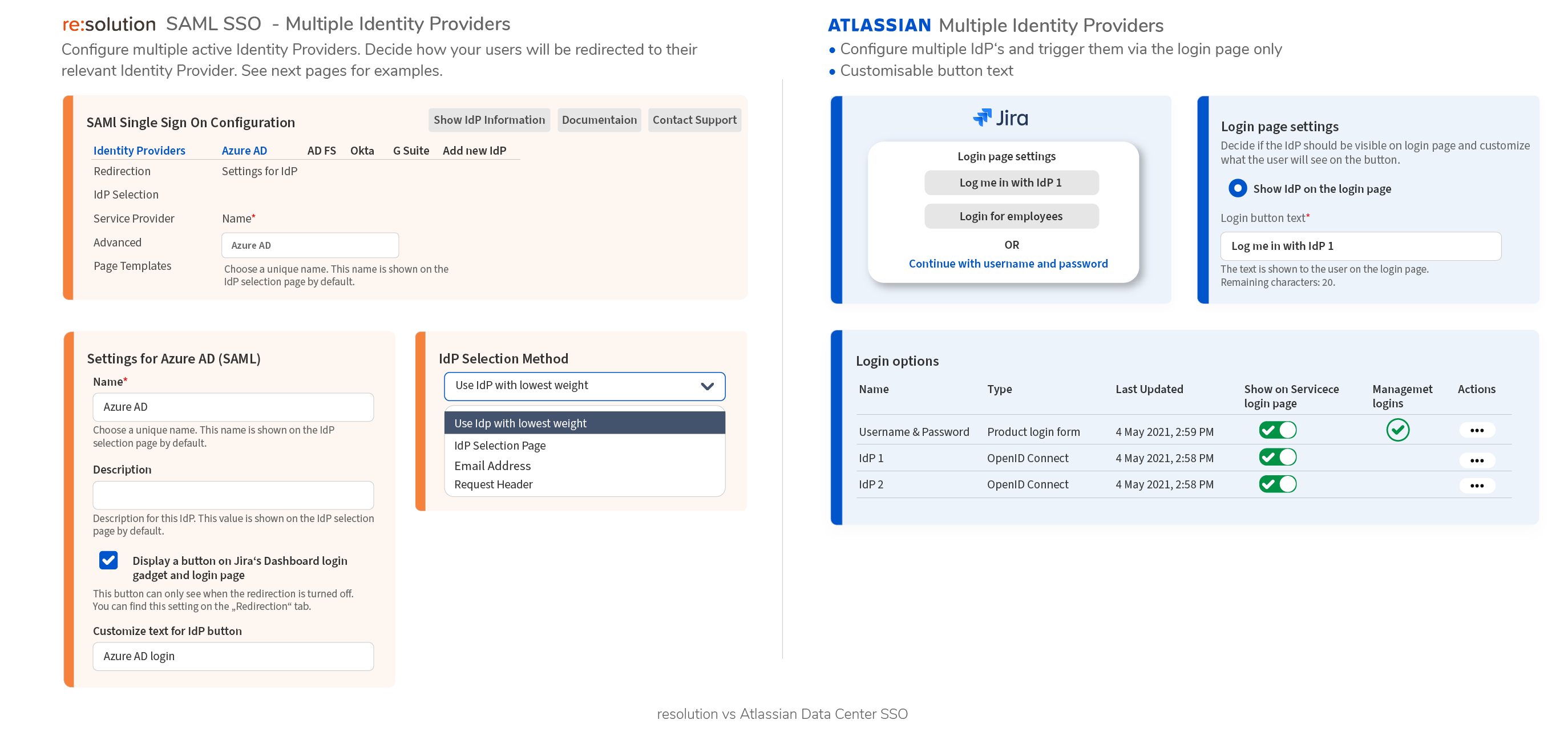
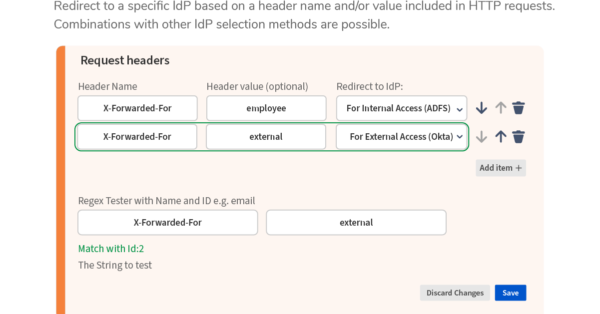
7. Setup Identity Providers (IdP)
Configure Multiple IdPs and its User-Facing Content
Further Examples (click to enlarge):
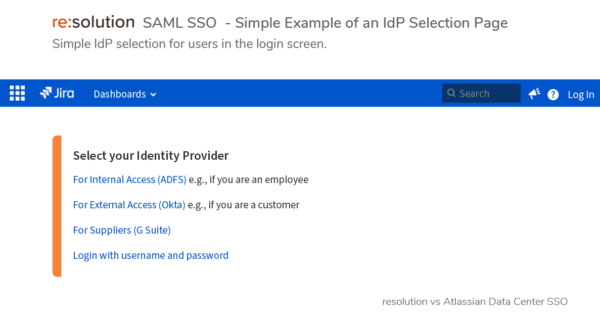
- Multiple IdPs can be configured in 4 ways to select IdP providers: choosing IdP by weight, by IdP selection page, by email address, by HTTP request headers. See examples above.
- Fully customizable IdP Selection Page, using velocity templates to comply with corporate branding and improve user experience.
- Provide customers flexibilities to handle scenarios, where some users need to login locally via Username/Passwords (e.g., Contractors) and others via one (or more) IdPs, some customers use > 100 IdPs.
- Decide if you want to display buttons per IdP in the login page, and customize the button text if you want to.
- When multiple IdPs are configured, they can only be selected by the user in the login page.
- IdPs with an active toggle will be shown in the login page as an additional button.
- The button text can be configured. No other customizations are possible.
8. Setup Service Provider
Signing and Encryption
- Include Signing Certificate in Metadata
- Include Encryption Certificate in Metadata
- The plugin supports both signed authentication requests and encryption of assertions. The above settings allow those to be added to the metadata as well
- Neither signed authentication requests nor encrypted SAML messages are supported
Want to stay upto date on the latest features for SAML SSO and how they compare to Atlassian’s built-in?
9. Advanced Settings
10. Customize User Facing Content
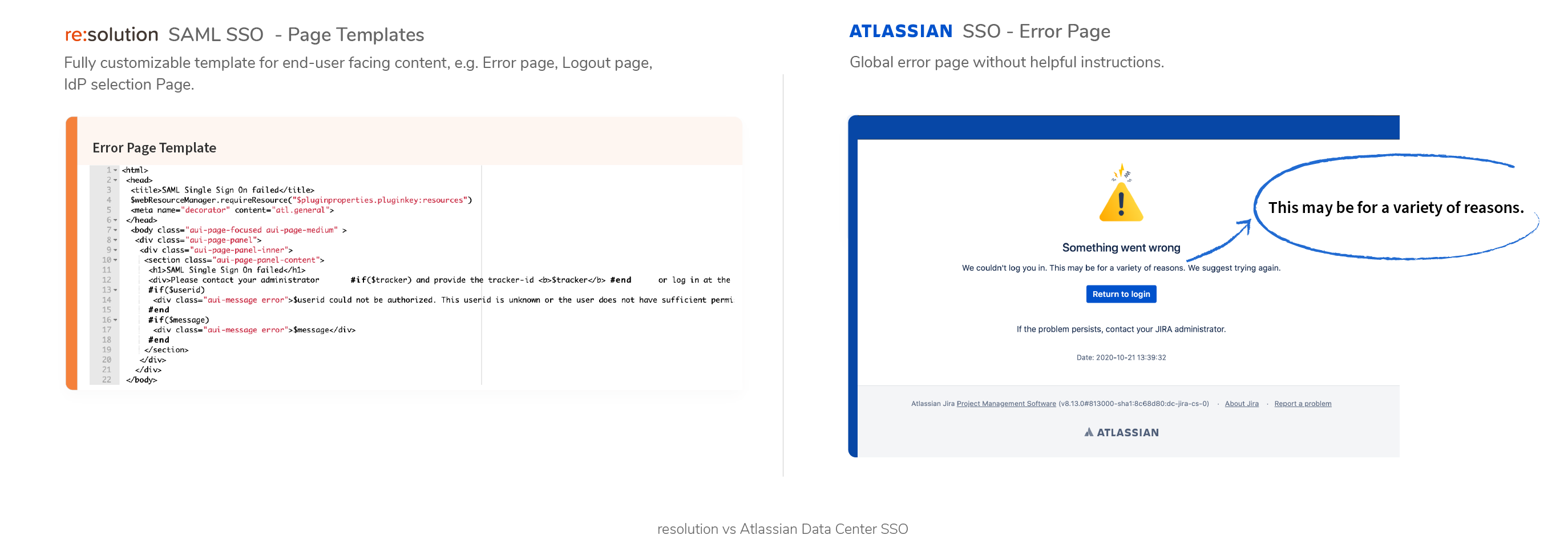
Setup Page Templates
- IdP selection Page(s)
- Error page
- Logout page
Read More
Not supported
11. Export/Import Configuration
12. Support - Authentication Tracker
Debugging Tracker & In-app Support
Built-in Support facility – Authentication Tracker
- History of all authentications in the last 48 hours
- Usually, no separate logging is required – all usual debug/info messages, including SAML request & response are contained in an authentication tracker
- Raise a support case straight from a tracker with the tracker & config being attached to the case
Book a call with our technical product experts
You want to see the apps in action. Perhaps you have started setting up the product and need help to better understand your options. Or maybe you need help configuring a complex scenario. Whatever the reason, our team will be happy to guide you.